51% Attack
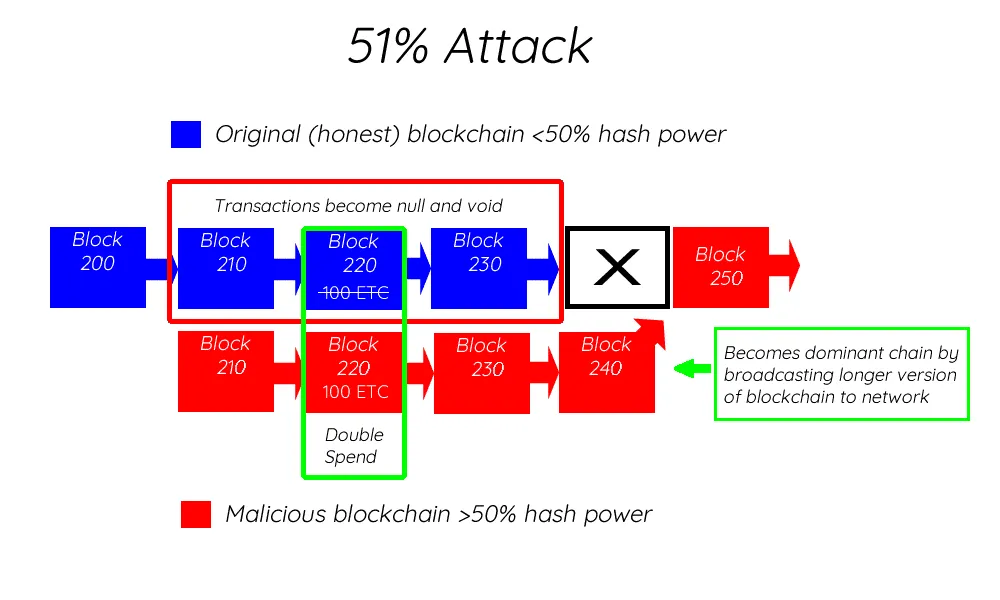
This is a PoW (Proof of Work) attack in which a (malicious) miner (or miners) contribute over 50% of the hashrate to a coins network. The network is open to this attack at an even lower % of hash, but a majority is often the given example. It’s keen to note that the attacker has to be a contributing miner to existing hashrate which has an economic price- “A PoW 51% attacker can significantly slow down the network, but even a single attempt to revert historical transactions requires a huge and long-running expense.” (Buterin, Medium 2017)
By controlling the majority of compute on the network, an attacker (or group of attackers) can interfere with the process of recording new blocks. They can prevent other miners from completing honest blocks, thereby allowing them to monopolize the mining of new blocks and earn all of the mining rewards.
This scenario assumes a breakdown in PoW miner diversity where the majority of mining would be owned by one malicious entity/group.
Three things are possible in this scenario:
- Prevent specific transactions from gaining confirmation
- Reverse transactions sent while the attacker is in control
- Prevent miners from finding blocks
What an attacker cannot do:
- Go into wallets
- Create new Bitcoins
- Destroy the network, but it does shake confidence
Thus this attack does have a ceiling – “You cannot do a protocol change even with 51% of the network. Even SPV nodes will reject your chain, and all you are doing is creating an airdrop copy of Bitcoin.” (Wright 2019)
Examples
Since 2016 this attack affected Krypton, Shift, Ethereum Classic, and Bitcoin Gold. In May 2018 Bitcoin Gold lost more than $18M due to this attack.
You can find up-to-date hashrate distribution among the largest mining pools here: https://www.blockchain.com/en/pools
References:
https://bitcointalk.org/index.php?topic=78403.msg874553#msg874553
https://craigwright.net/blog/bitcoin-blockchain-tech/economic-security/
Diagram: https://hackernoon.com/ethereum-classic-attacked-how-does-the-51-attack-occur-a5f3fa5d852e
« Back to Glossary Index